Looking for a code quality checklist?Answers to all your questions on code quality with the comprehensive checklist. Find out now 👈
The Invisible JavaScript Backdoor – Certitude Blog
wrangler 2.0 — a new developer experience for Cloudflare Workers
We’re excited to announce the second-generation of our developer tooling for Cloudflare Workers. It’s a new developer experience that’s out-of-the-box, lightning fast, and can even run Workers on a local machine. (Yes!)
Source: wrangler 2.0 — a new developer experience for Cloudflare Workers
How to Successfully Deploy Kubernetes Across Multi-Cloud Environments | D2iQ
offline først og database på klienten
A Pragmatic Approach to Live Collaboration – Hex Blog | Hex Technologies
or: How I Learned to Stop Worrying and Love the Atomic Operation
Source: A Pragmatic Approach to Live Collaboration – Hex Blog | Hex Technologies
Data Explorer – Axiom
Axiom Dashboard
Source: Data Explorer – Axiom
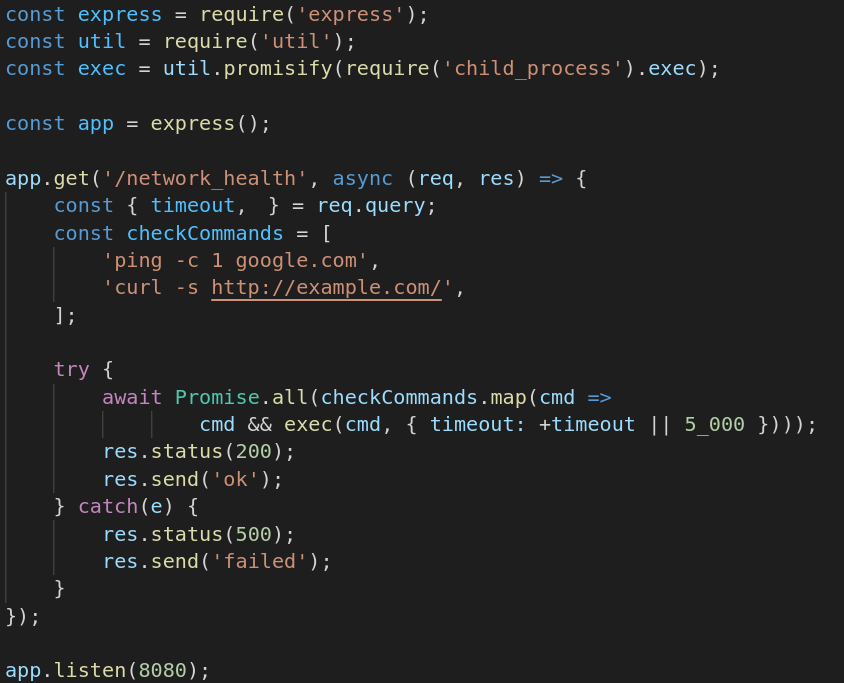
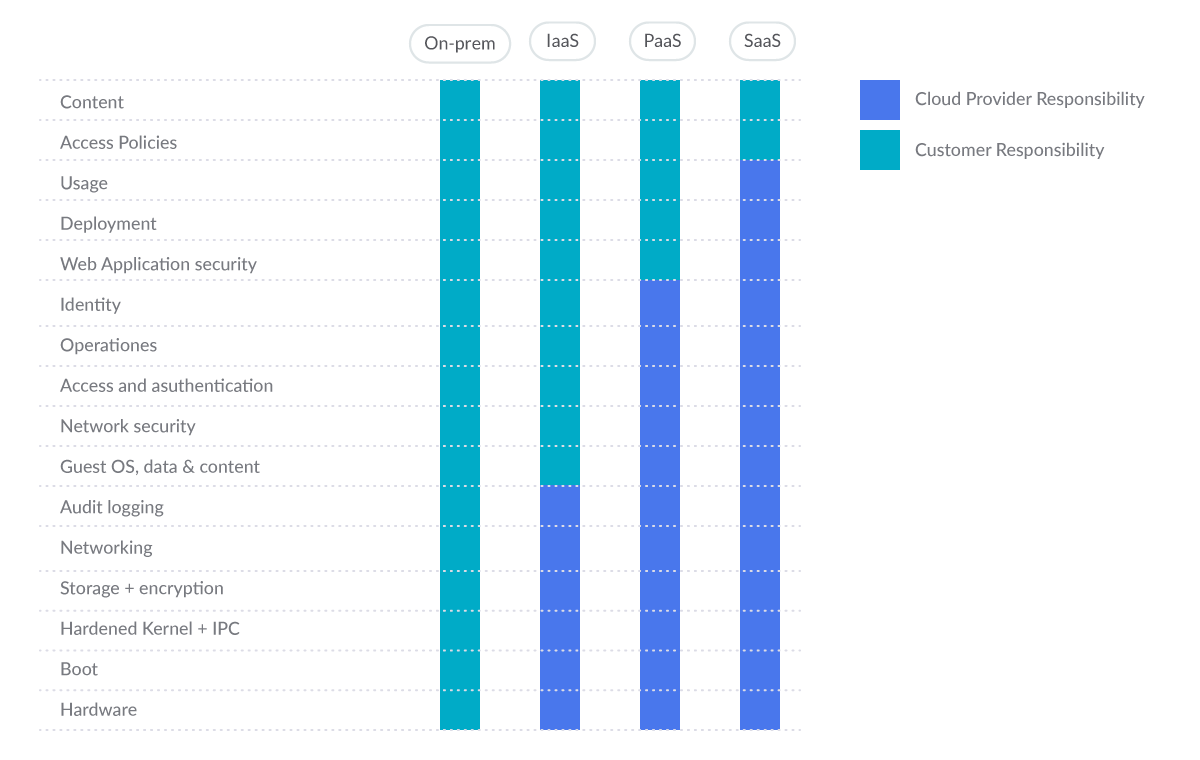
Container security best practices – Sysdig
Container security best practices include the full component stack used for building, distributing, and specifically executing the container.
A Comparison Of Serialization Formats | mbedded.ninja
A review of popular serialization formats (CSV, JSON, YAML, e.t.c), including speed and memory comparisons.
Source: A Comparison Of Serialization Formats | mbedded.ninja